Digital Signatures
This is a very brief explanation and example of how digital signatures work.
Tags: digital signatures
Posted in Instructional
This is a very brief explanation and example of how digital signatures work.
Tags: digital signatures
Posted in Instructional
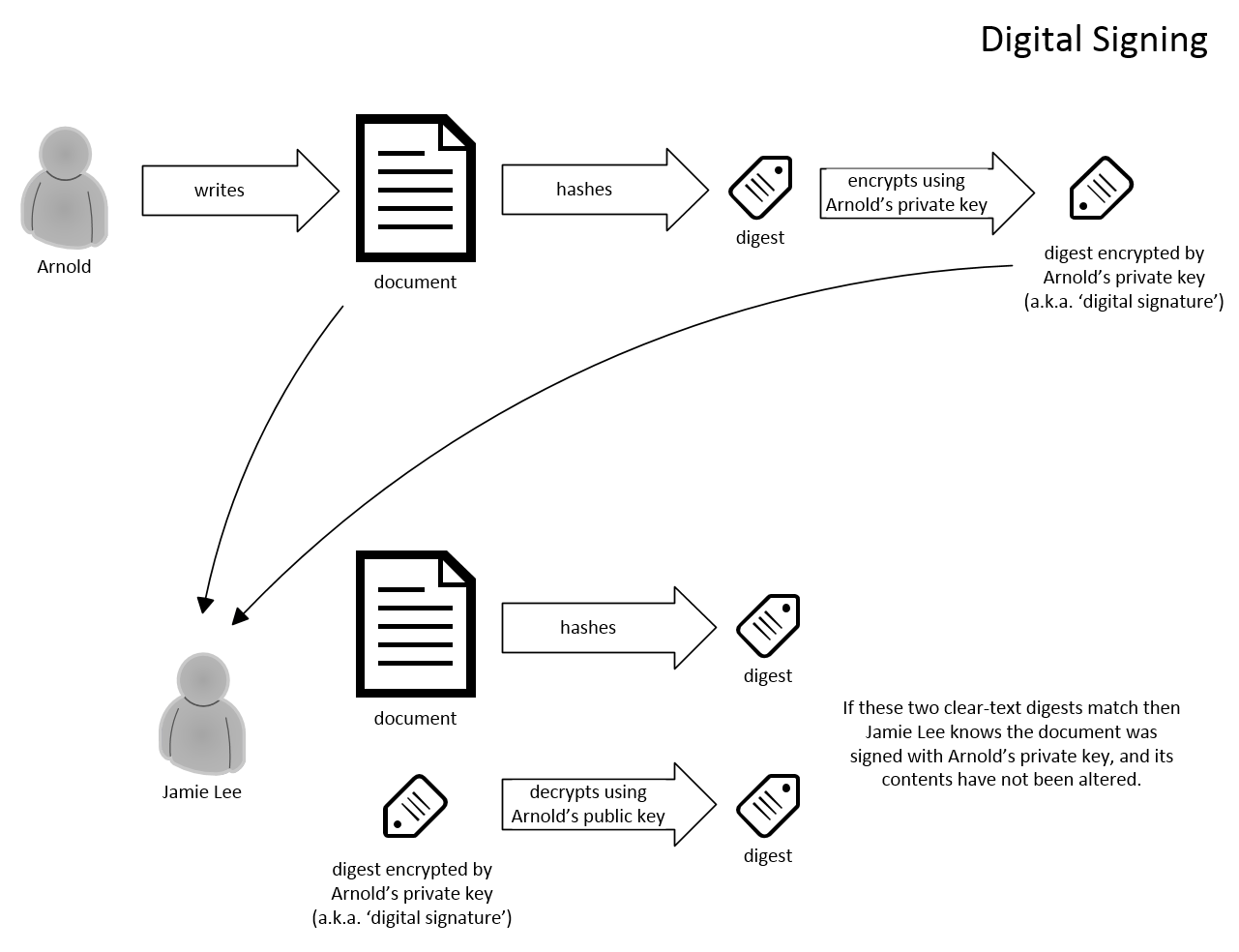
Thank you Mr. Benway for your contribution to IT community . I have two questions this video: (1) Jamie could decrypts Arnold’s digest . This means anything Arnold encrypts with his private key is not safe because his public key is available to attackers, right? It seems this method is used only for identification and Non-repudiation! (2) How can we be sure Arnold and Jamie are using the same hash algorithm? a digital certificate? Bye the way, your video with the title “Certificates on the Internet” is the best one in entire YouTube!! THANK YOU!
In response to your first question, if Arnold wanted to send Jamie Lee an encrypted file, he’d encrypt it with HER public key. Also, it’s likely that Arnold and Jamie Lee both have separate key pairs for different purposes; e.g. they would each have one key pair for their email signatures, one key pair for their highly confidential file transfers, etc., etc.. The digital signatures we’re talking about here are used to verify the identity of the originator, and to verify that the data has not been altered in transit. As for your second question, although I have not verified this I suspect that the hash algorithm is specified in the metadata of the digital signature.